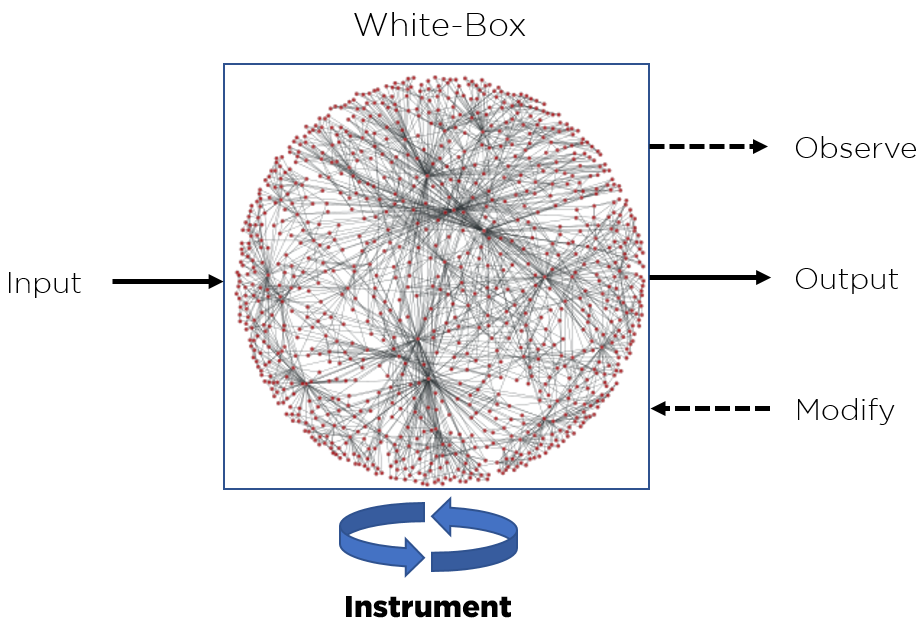
Implementation of White-Box Cryptography in Credit Card Processing Combined with Code Obfuscation | Semantic Scholar

How White-box Cryptography is gradually eliminating the hardware security dependency | by Terugu Venkat | Engineering Ezetap | Medium

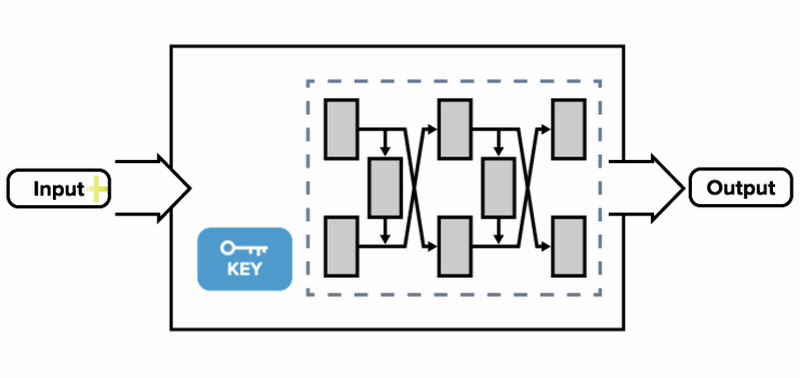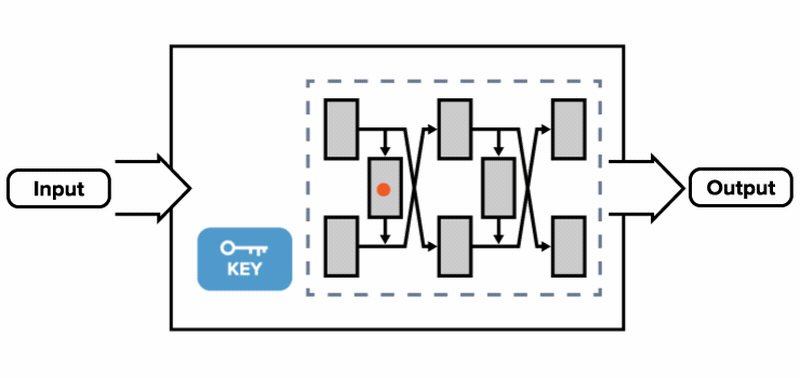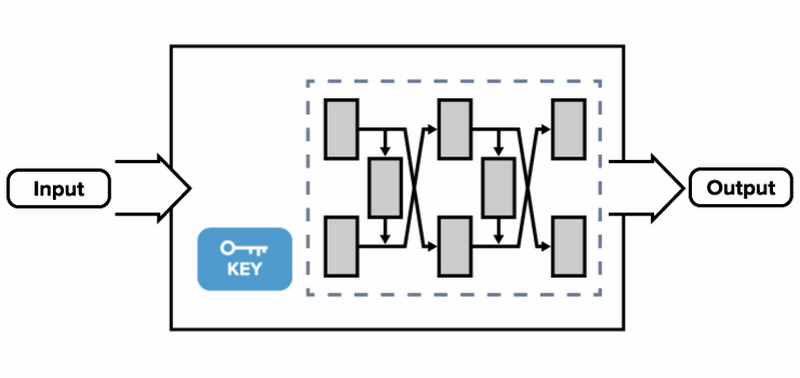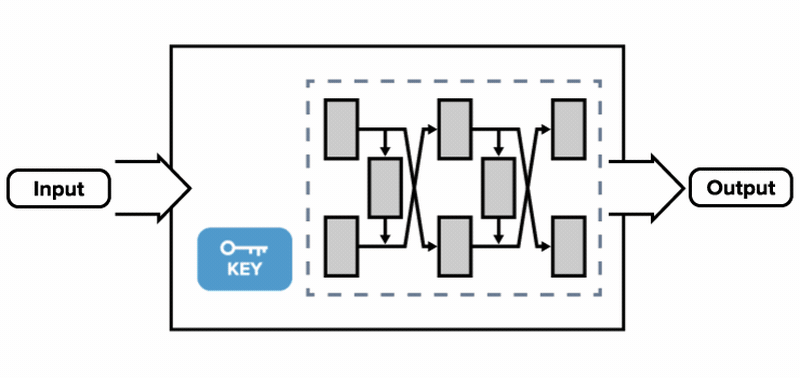
![PDF] WHITE-BOX CRYPTOGRAPHY : HIDING KEYS IN SOFTWARE | Semantic Scholar PDF] WHITE-BOX CRYPTOGRAPHY : HIDING KEYS IN SOFTWARE | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/370d9da733a85717974d09924ce3b3ca7a98c510/2-Figure1-1.png)

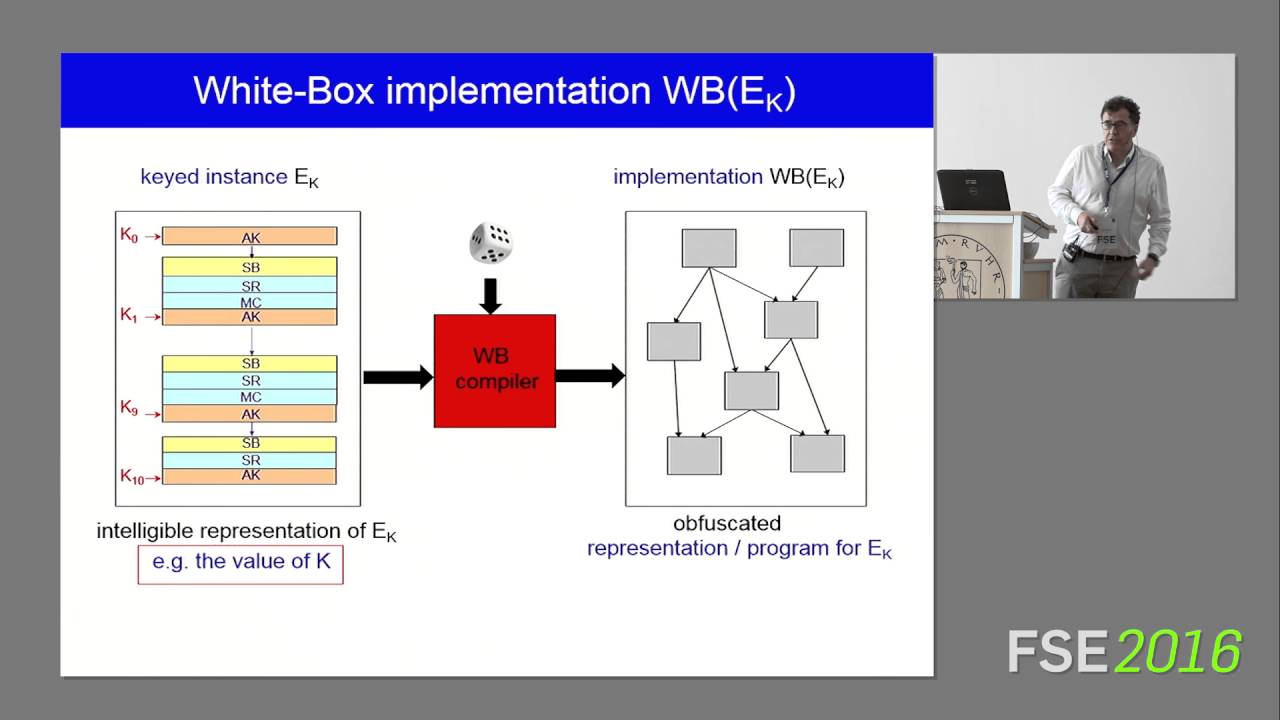

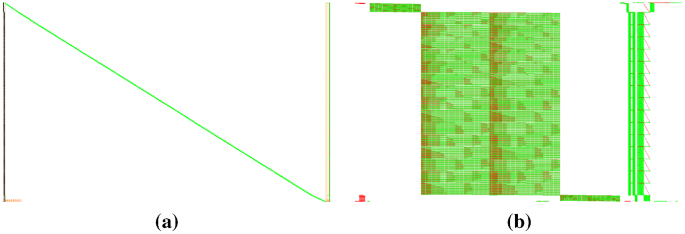
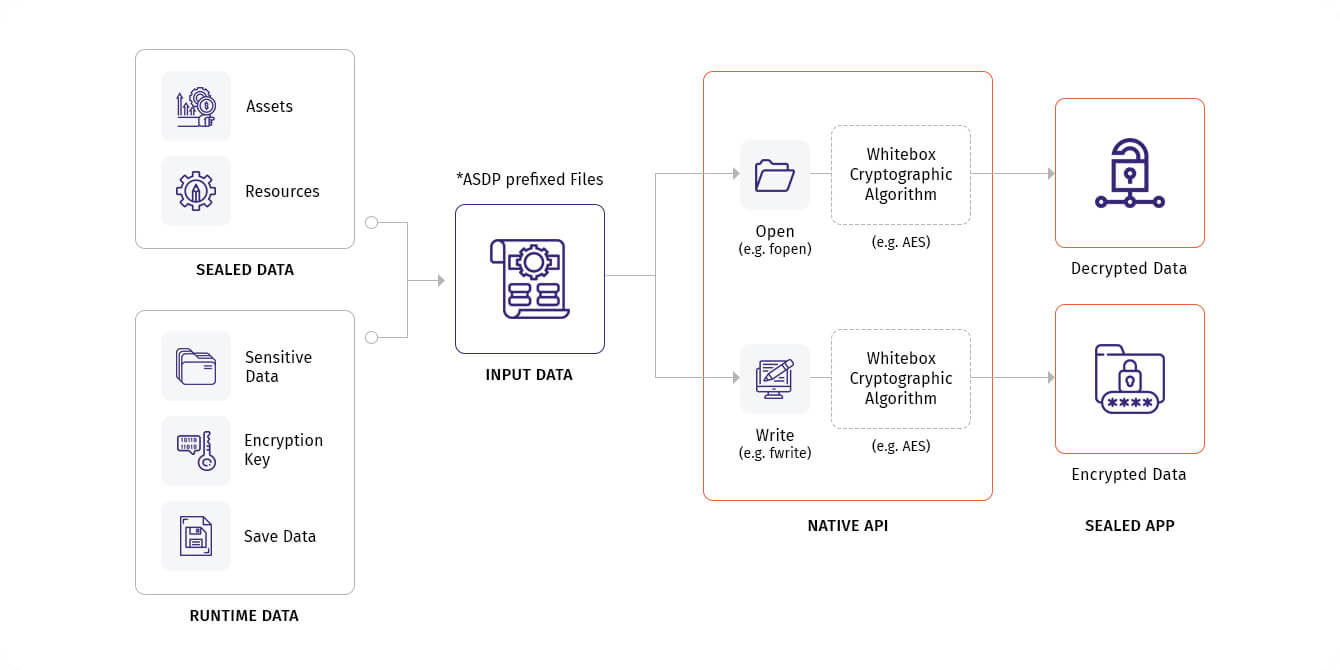


![PDF] WHITE-BOX CRYPTOGRAPHY : HIDING KEYS IN SOFTWARE | Semantic Scholar PDF] WHITE-BOX CRYPTOGRAPHY : HIDING KEYS IN SOFTWARE | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/370d9da733a85717974d09924ce3b3ca7a98c510/3-Figure2-1.png)